Configuring the Terraform MCP Server for Kilo Code
After jumping around AI coding agents for some time, I’ve been using Kilo Code for the past few months. I am very please with Kilo Code and in general, to be back into VS Code.
But I kept running into a familiar frustration: AI assistants making assumptions or suggesting outdated syntax. This isn’t unique to any specific language or framework — it’s a fundamental challenge when working with any tool that has strict structures, frequently updated documentation, or complex APIs. Whether you’re working with Terraform, Kubernetes manifests, API specifications, or framework configurations, the AI needs access to current, authoritative documentation to provide reliable assistance.
Connecting an Model Context Protocol (MCP) server can help with those issues.
The Documentation Gap
HashiCorp provides an official Terraform MCP server that can integrate with AI assistants to provide accurate, up-to-date Terraform documentation. However, the GitHub repository’s documentation focuses primarily on general MCP setup and doesn’t provide specific configuration examples for Kilo Code.
This left me spending more time than I should have figuring out the correct configuration format and Docker integration approach.
Why Use MCP Servers?
One outright benefit is fighting hallucinations. When an AI model has direct access to official documentation through MCP — whether for Terraform, programming languages, frameworks, or APIs — it can:
- Reference current schemas, APIs, and syntax
- Suggest code that follows the latest best practices
- Validate proposed changes against actual capabilities
- Provide accurate examples from official documentation
This approach applies universally: you could use MCP servers for Python libraries, cloud provider CLIs, database systems, or any tool with comprehensive documentation. The pattern is the same — give the AI authoritative context.
For Terraform specifically, this becomes valuable when working with providers that update frequently or have complex configuration requirements.
The Working Configuration
Here’s the configuration I’m using in Kilo Code’s MCP settings file (typically found in your Kilo Code configuration):
{
"mcpServers": {
"terraform": {
"command": "docker",
"args": [
"run",
"-i",
"--rm",
"-e",
"TFE_ADDRESS",
"-e",
"TFE_TOKEN",
"hashicorp/terraform-mcp-server:0.3.2"
],
"env": {
"TFE_ADDRESS": "https://app.terraform.io",
"TFE_TOKEN": ""
},
"disabled": true,
"alwaysAllow": []
}
}
}
Configuration Breakdown
Container runtime: The configuration uses docker as the command, but this works seamlessly with Podman as well. I like this approach to keeping the system clean and have to install MCP dependencies on the host itself. On my system, I’m actually running Podman with a Docker alias (alias docker=podman) in .zshrc (i favor ZSH), and the MCP server runs without any issues. If you’re using Podman, you don’t need to modify the configuration — the alias handles everything transparently.
Environment variables:
TFE_ADDRESS: Points to Terraform Cloud/Enterprise API endpoint (default:https://app.terraform.io)TFE_TOKEN: Your Terraform Cloud API token (leave empty if not using Terraform Cloud features)
Disabled by default: The "disabled": true flag means the server won’t start automatically. This is useful for controlling when the MCP server runs, as it consumes resources only when needed.
Version pinning: Using hashicorp/terraform-mcp-server:0.3.2 ensures consistent behavior. Check the Docker Hub repository for the latest version.
Setting It Up
-
Install Docker or Podman if you haven’t already (the MCP server runs as a container)
- If using Podman, set up the Docker alias:
alias docker=podman
- If using Podman, set up the Docker alias:
-
Add the configuration to your Kilo Code MCP settings file
-
Enable the server by changing
"disabled": falsein the configuration, or use Kilo Code’s MCP server management interface
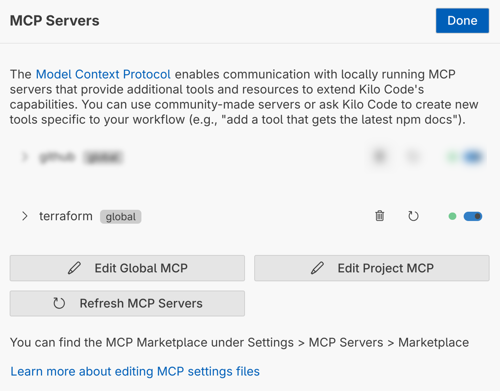 Screenshot: Activating the Terraform MCP server in Kilo Code’s settings~
Screenshot: Activating the Terraform MCP server in Kilo Code’s settings~
- Optional: Add Terraform Cloud token if you want to access private modules or Terraform Cloud-specific features
Real-World Impact
Since adding this configuration, I’ve noticed a significant improvement in the quality of Terraform suggestions from Kilo Code. The AI now references actual provider documentation when suggesting resource configurations, and I’ve caught several instances where it correctly warned me about deprecated attributes I was about to use.
I hope this helps!